1.5.5. I use basic ways to contrast negative interactions online (signalling posts to service owners, postal police etc.)
Experiencing negative outcomes online is increasingly common, with more people active online and the continued presence of aggressive online behaviors.
Negative online experience includes:
- personal abuse such as being the target of negative comments, cyberbullying, trolling or accessing disturbing content;
- theft of personal information including through accounts being hacked;
- fraud such as not receiving goods purchased online or these not being as described;
- spam, malware/viruses; and scams including ransomware;
- romance/dating or other financial scams where victims are tricked into sending money to criminals posing as others.
The nature of the online environment, characterised by a lack of face-to-face interactions, may lead to a paucity of cues that are normally used to detect malicious intentions or risky situations. People may be more easily misled by online cues, which can be falsified, such as fake online reviews. This thereby contributes to the risk of falling victim to cybercrime. The estimated annual cost of global cybercrime is estimated to be USD600 billion and nearly two-thirds of online users have experienced some form of victimisation (McAfee, 2018).
Internet use produces metadata, such as identifying information embedded in documents, which may be collected without consent and used to target individuals. Criminals also often exploit the tendency to share information by presenting deceptive sites to users directly or by hacking sites that collect personal information.
Overall Internet involvement does not predict victimisation, but specific activities are linked to certain harms. Namely: engagement with online pornography and forums; use of multiple discussion forums, dating, and gaming sites; and expenditure on gaming, dating and pornography sites.
What to do?
- Check your online accounts regularly.
- Check your bank account regularly and report any suspicious activity to your bank.
- Perform online payments only on secure websites (check the URL bar for the padlock and https) and use secure connections (choose a mobile network instead of public Wi-Fi).
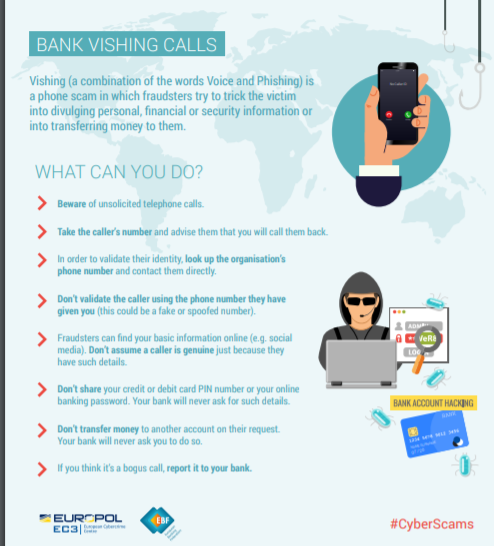
- Your bank will never ask you for sensitive information such as your online account credentials over the phone or email.
- If an offer sounds too good to be true, it’s almost always a scam.
- Keep your personal information safe and secure.
- Be very careful about how much personal information you share on social network sites. Fraudsters can use your information and pictures to create a fake identity or to target you with a scam.
- If you think that you have provided your account details to a scammer, contact your bank immediately.
- Always report any suspected fraud attempt to the police, even if you did not fall victim to the scam.
How To Combat The Negative Effects Of Social Media:
- Be mindful of your social media habits. ...
- Set limits on the amount of time you spend on social media. ...
- Know when it's time to stop scrolling. ...
- Use social media to connect with people who inspire you, share similar interests, and provide a sense of belonging.
How To Reduce Negative Effects Of Technology On Children:
- Monitor and limit the use of technology. It's of great importance to know how much and in what way your kid uses devices. ...
- Teach responsibility and conscious behavior. ...
- Keep up with the tech industry spin. ...
- Find alternatives to technology.
How Do I Report Something Online:
If you believe you're a victim of internet fraud or cybercrime, report it to the Internet Crime Complaint Center (IC3). Or, you can use the FBI's online tips form. Your complaint will be forwarded to federal, state, local, or international law enforcement.

More Informations Here: https://www.fbi.gov/investigate/cyber
How Does Police Catch Internet Crimes?
Law enforcement officials will use cyber forensic analysis tactics to find data and present it as evidence. Once the machines are obtained, cybercrime units are assembled, which have special technical skills. The cybercrime unit decrypts files, reveals passwords, seizes information, and recovers missing files.

How Do You Verify A Post?
Look for a Blue Check Mark.
If the content is posted by what appears to be the original author, look to see that it is from a verified account, which is signified by a blue checkmark next to the account name.
How Do You Verify A Source?
- Identify the source of the information and determine whether it is reliable and credible.
- Checking sources for validity against other reliable sources.
- Is the information presented in a biased way?
- Search for citations that support the claims made by the author or organization.